Analisti di sicurezza informatica | Incident Responder | Specialista SecOps
+10 anni di esperienza in sicurezza di rete e informatica. Appassionato di sicurezza informatica
Attacchi informatici in cifre
Organizzazioni di tutte le dimensioni sono un bersaglio
La tecnica rende necessaria la formazione del personale interno.
Il costo del ransomware, che potrebbe portare a difficoltà finanziarie o al fallimento.
Si stima $265 miliardi entro il 2031
Evidenzia l’importanza dei dati dei clienti.
L’avvento ai tempi del Covid 19 del lavoro da casa ha aperto le porte a più vulnerabilità di sicurezza.
Negli ultimi 3 anni. Il costo medio dei danni causati dagli attacchi informatici è aumentato del 42%.
Indicano più vulnerabilità e misure di sicurezza.
A causa dei gravi impatti che potrebbero emergere, la resposnabilità ricade su figure C-level, come emerge dalle risposte alla survey di Gartner
Attacchi informatici in cifre
Organizzazioni di tutte le dimensioni sono un bersaglio
La tecnica rende necessaria la formazione del personale interno.
Il costo del ransomware, che potrebbe portare a difficoltà finanziarie o al fallimento.
Si stima $265 miliardi entro il 2031
Evidenzia l’importanza dei dati dei clienti.
L’avvento ai tempi del Covid 19 del lavoro da casa ha aperto le porte a più vulnerabilità di sicurezza.
Negli ultimi 3 anni. Il costo medio dei danni causati dagli attacchi informatici è aumentato del 42%.
Indicano più vulnerabilità e misure di sicurezza.
A causa dei gravi impatti che potrebbero emergere, la resposnabilità ricade su figure C-level, come emerge dalle risposte alla survey di Gartner
Una relazione basata su obiettivi condivisi

Una relazione basata su obiettivi condivisi

Panoramica
Panoramica
Il modello Make IT – Monitoraggio e rilevamento
Identificazione e valutazione delle potenziali minacce su infrastruttura, sistemi, rete, dati e app in esecuzione.
Comprensione più approfondita dei potenziali rischi, del dominio e delle caratteristiche.
Piattaforme di Threat Intelligence (CTI) Strumenti di analisi malware
Attività proattive per mitigare i potenziali rischi e rafforzare la postura di sicurezza.
EDR, firewall, sistemi di autenticazione multi-fattore, sistemi di crittografia dei dati
Monitoraggio costante dell’infrastruttura IT
Sistemi di rilevamento delle intrusioni (IDS)
Sistemi di prevenzione delle intrusioni (IPS)
Sistemi di gestione degli Security Event (SIEM)
Firewall per applicativi (WAF)
Sicurezza di cloud e container
Flusso regolare di comunicazione tra tutte le parti interessate
Piattaforme di gestione dei casi di sicurezza (strumenti di ticketing),
Sistemi di gestione della documentazione.
Protocolli progettati per gestire efficacemente e ridurre l’impatto di / prevenire incident di sicurezza in tempo reale.
Sistemi di risposta agli incident
Piattaforme di orchestrazione degli incident (SOAR).
Strumenti di reportistica e pratiche di documentazione.
Supporto continuo in tutte le questioni relative alla sicurezza.
Garantire che le parti interessate siano consapevoli dei fondamenti/protocolli.
Sistemi di gestione della conoscenza
Strumenti di formazione online
The make it model – Monitoring and detecting
Identificazione e valutazione delle potenziali minacce su infrastruttura, sistemi, rete, dati e app in esecuzione.
Comprensione più approfondita dei potenziali rischi, del dominio e delle caratteristiche.
Piattaforme di Threat Intelligence (CTI) Strumenti di analisi malware
Attività proattive per mitigare i potenziali rischi e rafforzare la postura di sicurezza.
EDR, firewall, sistemi di autenticazione multi-fattore, sistemi di crittografia dei dati
Monitoraggio costante dell’infrastruttura IT
Sistemi di rilevamento delle intrusioni (IDS)
Sistemi di prevenzione delle intrusioni (IPS)
Sistemi di gestione degli Security Event (SIEM)
Firewall per applicativi (WAF)
Sicurezza di cloud e container
Flusso regolare di comunicazione tra tutte le parti interessate
Piattaforme di gestione dei casi di sicurezza (strumenti di ticketing),
Sistemi di gestione della documentazione.
Protocolli progettati per gestire efficacemente e ridurre l’impatto di / prevenire incident di sicurezza in tempo reale.
Sistemi di risposta agli incident
Piattaforme di orchestrazione degli incident (SOAR).
Strumenti di reportistica e pratiche di documentazione.
Supporto continuo in tutte le questioni relative alla sicurezza.
Garantire che le parti interessate siano consapevoli dei fondamenti/protocolli.
Sistemi di gestione della conoscenza
Strumenti di formazione online
Il modello Make IT – Penetrazione
Stare al passo con le minacce emergenti e superare i tentativi di intrusione
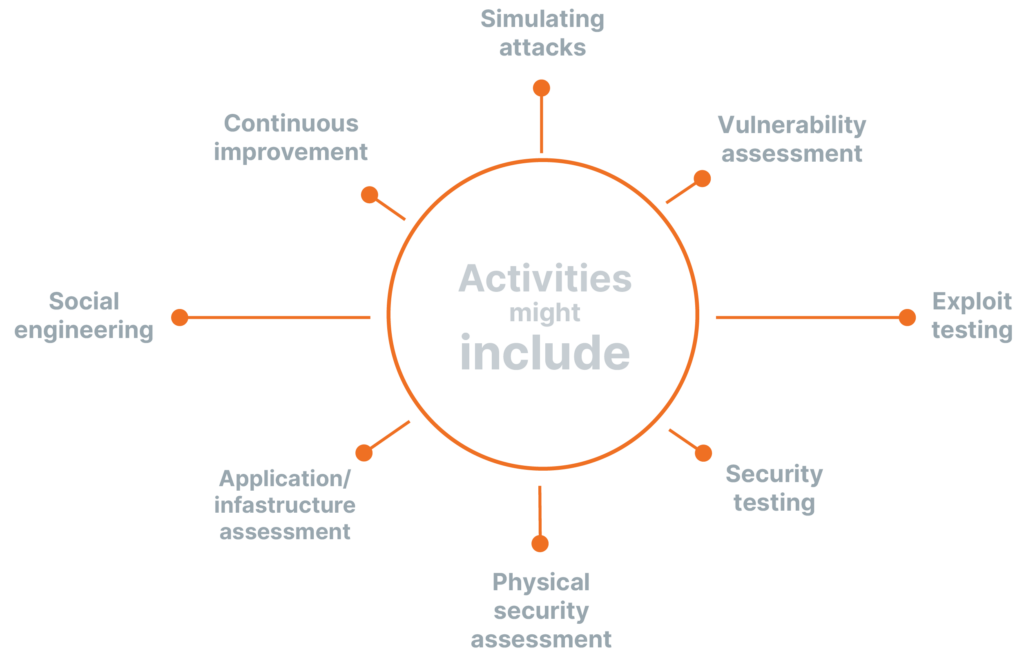
Il modello Make IT – Penetrazione
Stare al passo con le minacce emergenti e superare i tentativi di intrusione

Esperti in sicurezza informatica dalla metà degli anni ’90

Sircle dedicati che si rivolgono a varie aree della sicurezza
Un team leggendario in campo
Ore di formazione
Gestione completa delle attività di sicurezza di enti di spicco, in vari settori, in Europa, Stati Uniti e Africa.
Supporto della community e sviluppo di vari strumenti open source relativi alla sicurezza
Supporto 24 ore su 24, 7 giorni su 7, 365 giorni all’anno

Massimo accreditamento sul campo
Esperienza pratica e accreditamento applicativi
Esperti in sicurezza informatica dalla metà degli anni ’90

Sircle dedicati che si rivolgono a varie aree della sicurezza
Un team leggendario in campo
Ore di formazione
Gestione completa delle attività di sicurezza di enti di spicco, in vari settori, in Europa, Stati Uniti e Africa.
Supporto della community e sviluppo di vari strumenti open source relativi alla sicurezza
Supporto 24 ore su 24, 7 giorni su 7, 365 giorni all’anno

Massimo accreditamento sul campo
Esperienza pratica e accreditamento applicativi

Analisti di sicurezza informatica | Incident Responder | Specialista SecOps
+10 anni di esperienza in sicurezza di rete e informatica. Appassionato di sicurezza informatica

Consulente per la sicurezza delle applicazioni
+7 anni di esperienza nel campo della sicurezza. CTF player, cacciatore di bug e appassionato di sicurezza informatica.











Da tecnologie/vendor, livelli di competenza, domini/specializzazioni IT, passando per certificazioni indipendenti dal vendor
ISO 27001 | ISO 20000-1 | ISO 9001 | ITIL
| 3CX |
| 6sigma |
| Aerohive |
| Aerohive Networks |
| Alison |
| ALTARO |
| Amazon |
| AMPG International |
| APMG |
| Apple |
| Aruba |
| AXELOS |
| Barracuda |
| BIT |
| Blue Team |
| BMC |
| Brocade |
| Business Objects |
| CEPIS |
| CertProf |
| Check Point |
| Cisco |
| Citrix |
| Cloud Champion |
| Cloudera |
| Cobit |
| COMMVAULT |
| Company Tutor |
| Compaq |
| CompTIA |
| CROSSNOVA |
| CSSC |
| Cyberark |
| D-LINK |
| Databricks Academy |
| DataCore |
| DELL EMC |
| Devops Institute |
| Dynatrace |
| Ec-Council |
| ECDL |
| Edx |
| eipass |
| Elastic |
| eLearnSecurity |
| EMC |
| EnterpriseDB |
| enVision |
| EUCIP |
| EXIN |
| Extreme Networks |
| F5 |
| FacilityLive |
| FinOps Foundation |
| FireEye |
| ForeScout |
| FORTINET |
| GIAC |
| GitLAB |
| Google Cloud |
| Google Play Academy |
| HashiCorp |
| Hazelcast |
| Hitachi |
| HP |
| Huawei |
| IBM |
| Infoblox |
| INIM Eletronics |
| Istituto Italiano di Project Management |
| ISTQB |
| Juniper |
| Konnex |
| Lacework |
| LibraEsva |
| Linux Foundation |
| Linux Professional Institute |
| MariaDB |
| Meru |
| MIA-PLATFORM |
| Microsoft |
| MikroTik |
| MongoDB |
| Neo4j |
| NetApp |
| Netscreen |
| Netskope |
| Netwitness |
| NETWRIX |
| Novell |
| NUTANIX |
| ObserveIT |
| Offensive Security |
| OpenSecurityTraining2 |
| ORACLE |
| Palo Alto |
| People Cert |
| PMI |
| Qualys |
| Rancher Academy |
| Red Hat |
| Reevo Cloud Academy |
| Reuters |
| SCP |
| Scrum Alliance |
| Scrum.org |
| ScrumStudy |
| SonicWall |
| SOPHOS |
| Splunk |
| Stormagic |
| Sun |
| SUSE |
| Symantec |
| TERADATA |
| Toshiba |
| Trend Micro |
| Triton |
| Veeam |
| Vendor |
| Veritas |
| VMware |
| WatchGuard |
| WatchGuardONE |
| WEBROOT University |
| ZERTO |
| ZyXEL |
Aree e campi di interesse
Visione a 360° 24 ore su 24
Attività SOC
Analisi approfondita della postura del progetto, consapevolezza del team e strategia personalizzata per il futuro.
Processi, metodologie, strumenti e workshop
Esecuzione, reporting e consulenza.
Potrebbe includere la successiva gestione dei problemi rilevati.
Governance della sicurezza informatica
Aree e campi di interesse
Visione a 360° 24 ore su 24
Attività SOC
Analisi approfondita della postura del progetto, consapevolezza del team e strategia personalizzata per il futuro.
Processi, metodologie, strumenti e workshop
Esecuzione, reporting e consulenza.
Potrebbe includere la successiva gestione dei problemi rilevati.
Governance della sicurezza informatica
Fornito da: SORINTians
Penetration testing black-box – Estensione WP
Durante lo svolgimento di attività di penetration test per la soluzione web di un cliente. Il nostro team di sicurezza è stato in grado di rilevare un bug XSS critico per l’estensione WP-Optimize (+1 milione di installazioni attive). Sviluppato dal Team UpdraftPlus. Un noto plugin di WordPress.
Il bug è stato documentato e segnalato ai provider.
In sintesi, la sfida era complicata da dimostrare. Richiedeva strumenti/estensioni (WPScan, WordFence Security e altri) diversi tentativi, l’iniezione di payload, il sondaggio della funzione di ricerca utilizzando Burp Intruder come attacco, oltre a perfezionare le tattiche di attacco. Dopo alcuni tentativi, siamo stati in grado di ottenere il payload XSS-reflected.
Il team è stato in grado di analizzare come l’opzione WebP-Conversion causasse un flusso durante il processo di conversione delle entità HTML nei caratteri HTML riservati. Chiaramente un problema. Gli aggressori possono così iniettare input dannosi codificati utilizzando entità HTML e la funzione str_get_html. La funzione lo riconvertirà in tag HTML effettivi, dove il browser sarà in grado di renderizzarlo, bypassando il filtro Wordfence, che avviene prima della funzione str_get_html.
Risultato e consegna
Soluzione EDR, progettazione e implementazione per tutti gli endpoint
Trovare, configurare e implementare uno strumento EDR (Endpoint Detection & Response). Per centinaia di migliaia di endpoint.
La fase di indagine si è concentrata profondamente sull’analisi del cliente, infrastruttura e valutazione dei possibili strumenti rilevanti, con conseguente gruppo di POC e test, insieme a una chiara
proposta di implementazione.
Dopo la fase di selezione dello strumento, la fase di implementazione includeva attività come:
Attività volte a fornire visibilità in tempo reale delle minacce rilevate e a isolarle dalla rete. Fornire un’analisi accurata.
Risultato e consegna
Implementation and Management of a SIEM Solution
A SIEM tool able to:
Evaluating client’s SOC and NOC workflow during the
tool selection phase. Closely aligning with client’s internal team.
Following the evaluation process and the agreement on the proposal submitted. SIEM Elastic was the go-to- choice due to the capability of being a modular/unified, scalable, and on top, being an open-source solution. Importantly, allowing SOC analysts to conduct swiftly analytical security events. Furthermore, the implementation phase carried out activities like:
Result & delivery
Within the agreed timeframes, a high-quality software product that fully complied to all pre-planned requirements. E.g.
Fornito da: SORINTians
Penetration testing black-box – Estensione WP
Durante lo svolgimento di attività di penetration test per la soluzione web di un cliente. Il nostro team di sicurezza è stato in grado di rilevare un bug XSS critico per l’estensione WP-Optimize (+1 milione di installazioni attive). Sviluppato dal Team UpdraftPlus. Un noto plugin di WordPress.
Il bug è stato documentato e segnalato ai provider.
In sintesi, la sfida era complicata da dimostrare. Richiedeva strumenti/estensioni (WPScan, WordFence Security e altri) diversi tentativi, l’iniezione di payload, il sondaggio della funzione di ricerca utilizzando Burp Intruder come attacco, oltre a perfezionare le tattiche di attacco. Dopo alcuni tentativi, siamo stati in grado di ottenere il payload XSS-reflected.
Il team è stato in grado di analizzare come l’opzione WebP-Conversion causasse un flusso durante il processo di conversione delle entità HTML nei caratteri HTML riservati. Chiaramente un problema. Gli aggressori possono così iniettare input dannosi codificati utilizzando entità HTML e la funzione str_get_html. La funzione lo riconvertirà in tag HTML effettivi, dove il browser sarà in grado di renderizzarlo, bypassando il filtro Wordfence, che avviene prima della funzione str_get_html.
Risultato e consegna
Soluzione EDR, progettazione e implementazione per tutti gli endpoint
Trovare, configurare e implementare uno strumento EDR (Endpoint Detection & Response). Per centinaia di migliaia di endpoint.
La fase di indagine si è concentrata profondamente sull’analisi del cliente, infrastruttura e valutazione dei possibili strumenti rilevanti, con conseguente gruppo di POC e test, insieme a una chiara
proposta di implementazione.
Dopo la fase di selezione dello strumento, la fase di implementazione includeva attività come:
Attività volte a fornire visibilità in tempo reale delle minacce rilevate e a isolarle dalla rete. Fornire un’analisi accurata.
Risultato e consegna
Implementation and Management of a SIEM Solution
A SIEM tool able to:
Evaluating client’s SOC and NOC workflow during the
tool selection phase. Closely aligning with client’s internal team.
Following the evaluation process and the agreement on the proposal submitted. SIEM Elastic was the go-to- choice due to the capability of being a modular/unified, scalable, and on top, being an open-source solution. Importantly, allowing SOC analysts to conduct swiftly analytical security events. Furthermore, the implementation phase carried out activities like:
Result & delivery
Within the agreed timeframes, a high-quality software product that fully complied to all pre-planned requirements. E.g.





Welisten
24x7x365
Welisten
24x7x365
