The need of container security
Trillion
Trillion
Trillion
A Raised Concern
Container environment are rapidly moving to production
In 2021, less than 40% of global organization ran containerized applications in production. 90% by 2027
The attack surface is increasing
Attackers are targeting the misconfiguration of cloud infrastructure (network, storage, identities and permissions), APIs and the software supply chain itself. Gartner 2023
Knowledge & Awareness
K8s abstracts container networking, trading off the network security.
Tools
Traditional tools do not work with containerized environment. New tools and practices emerge every day.
A Raised Concern
The need of container security
Container environment are rapidly moving to production
In 2021, less than 40% of global organization ran containerized applications in production.
90% by 2027
The attack surface is increasing
Attackers are targeting the misconfiguration of cloud infrastructure (network, storage, identities and permissions), APIs and the software supply chain itself. Gartner 2023
Knowledge & Awareness
K8s abstracts container networking, trading off the network security.
Tools
Traditional tools do not work with containerized environment. New tools and practices emerge every day.
Cloud Native vs Traditional
Cost of dynamic approach
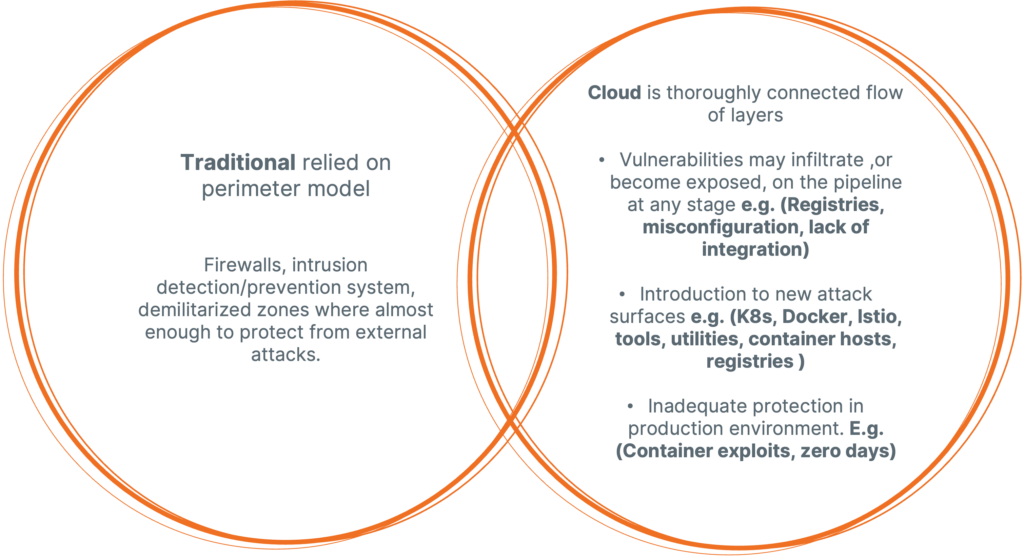
Cloud Native vs Traditional
Cost of dynamic approach

SORINT.lab’s Tailored Journey
The make it model
SORINT.lab’s Tailored Journey
The make it model
SORINT.lab’s Tailored Journey
Instantiated from
Every journey is a unique challenge, but our know-how:
Executed countless projects in the field to prominent entities in Europe, US, and Africa.
For various industries

Customer retention rate

Dedicated sircles specialized in given fields and technologies

Highest certification in various fields and “Training Partner” to some vendors
Expert PM with technical background ensuring project’s objectives are met
SORINT.lab’s Tailored Journey
Instantiated from
Every journey is a unique challenge, but our know-how:
Executed countless projects in the field to prominent entities in Europe, US, and Africa.
For various industries

Customer retention rate

Dedicated sircles specialized in given fields and technologies

Highest certification in various fields and “Training Partner” to some vendors
Expert PM with technical background ensuring project’s objectives are met
Experts Involved
Prestigious Certificates







Other sircles and specialisations involved






Closer Look
Areas and fields of focus
- Analysis, architect, consultant, and implement.
- Tailored proposals. Based on project and client’s needs.
- Where our security experts advise and hand-on workshops, training, knowledge, solutions, assess the security posture and much more.
- Offer experts in given fields or technologies.
Closer Look
Areas and field of focus
- Analysis, architect, consultant, and implement.
- Tailored proposals. Based on project and client’s needs.
- Where our security experts advise and hand-on workshops, training, knowledge, solutions, assess the security posture and much more.
- Offer experts in given fields or technologies.
Success Stories
Delivered by: SORINTians
Introducing a New Tool and Integration
- Pre-defined infrastructure.
- Running two OS. Linux and Windows.
- Solid compatibility integration with vSphere.
- Enables security operators to handle potential threats and security notification from a centralized console.
Result & delivery (UTD)
- Installed and integrated the new solution.
- Secured and centralized the monitoring of 500 systems with Carbon Black.
- Carried out test through injecting both OS with malware. All successfully identified.
- Alignment workshop with client’s team.
- Single product with no extensions was a major success to client’s needs.
Success Stories
Delivered by: SORINTians
Introducing a New Tool and Integration
- Pre-defined infrastructure.
- Running two OS. Linux and Windows.
- Solid compatibility integration with vSphere.
- Enables security operators to handle potential threats and security notification from a centralized console.
Result & delivery (UTD)
- Installed and integrated the new solution.
- Secured and centralized the monitoring of 500 systems with Carbon Black.
- Carried out test through injecting both OS with malware. All successfully identified.
- Alignment workshop with client’s team.
- Single product with no extensions was a major success to client’s needs.
Related Solutions and Tools by SORINTians


Welisten
24x7x365
Welisten
24x7x365



